Your Data, Our Priority: Advanced Security Solutions
Data Security Between Parties
Both parties sign a data confidentiality agreement to ensure data security and prevent resale.
Operator Security Awareness
A professional legal team establishes strict data security protocols and conducts periodic training. Operators must pass assessments before starting work.
Data Collection Compliance
For user information, authorization agreements are signed to ensure legal privacy rights.
Employee Confidentiality
Sign confidentiality agreements with employees.
User Authentication
Authenticate users via SMS or Email.
Access Restrictions
Prohibit simultaneous logins from multiple devices to prevent unauthorized access.
Permission Management
Implement RBAC (Role-Based Access Control) to strictly control functional and data permissions.
Operation Audit
Monitor data viewing and operational records.
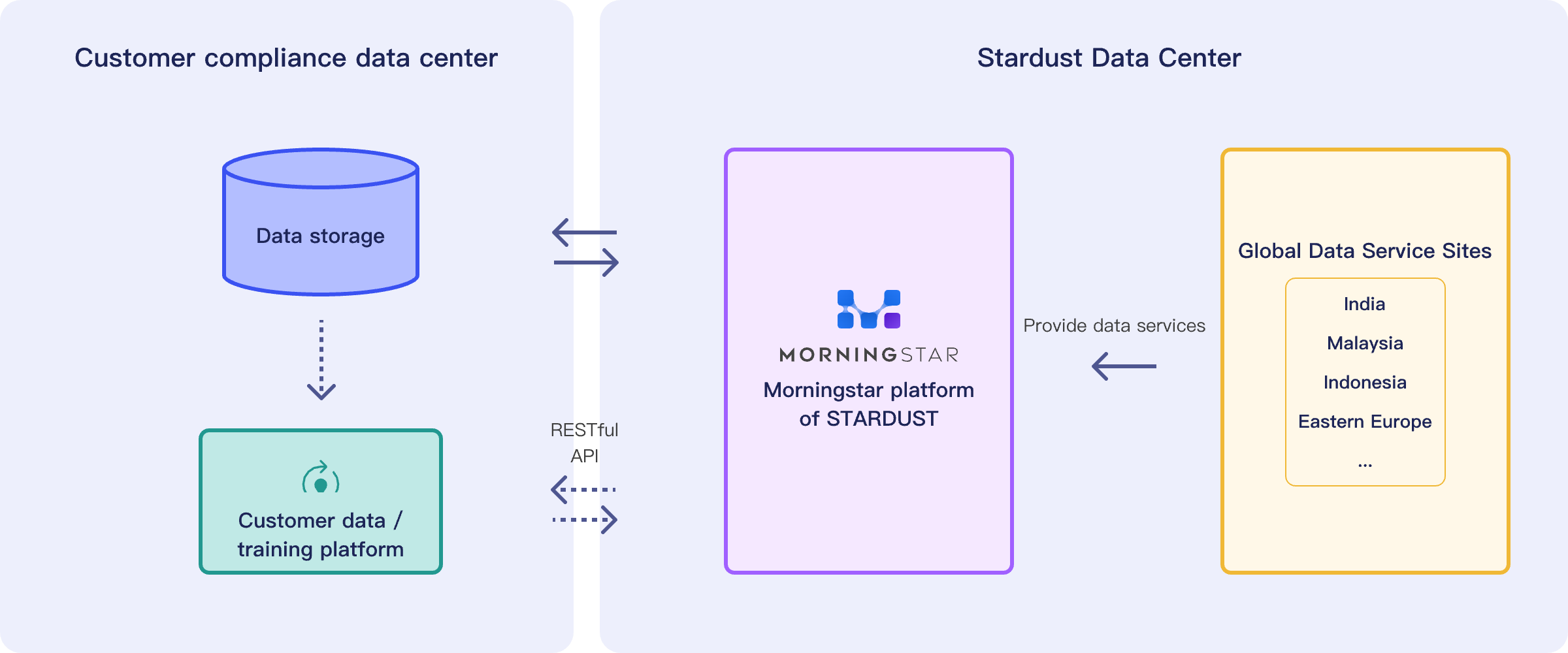
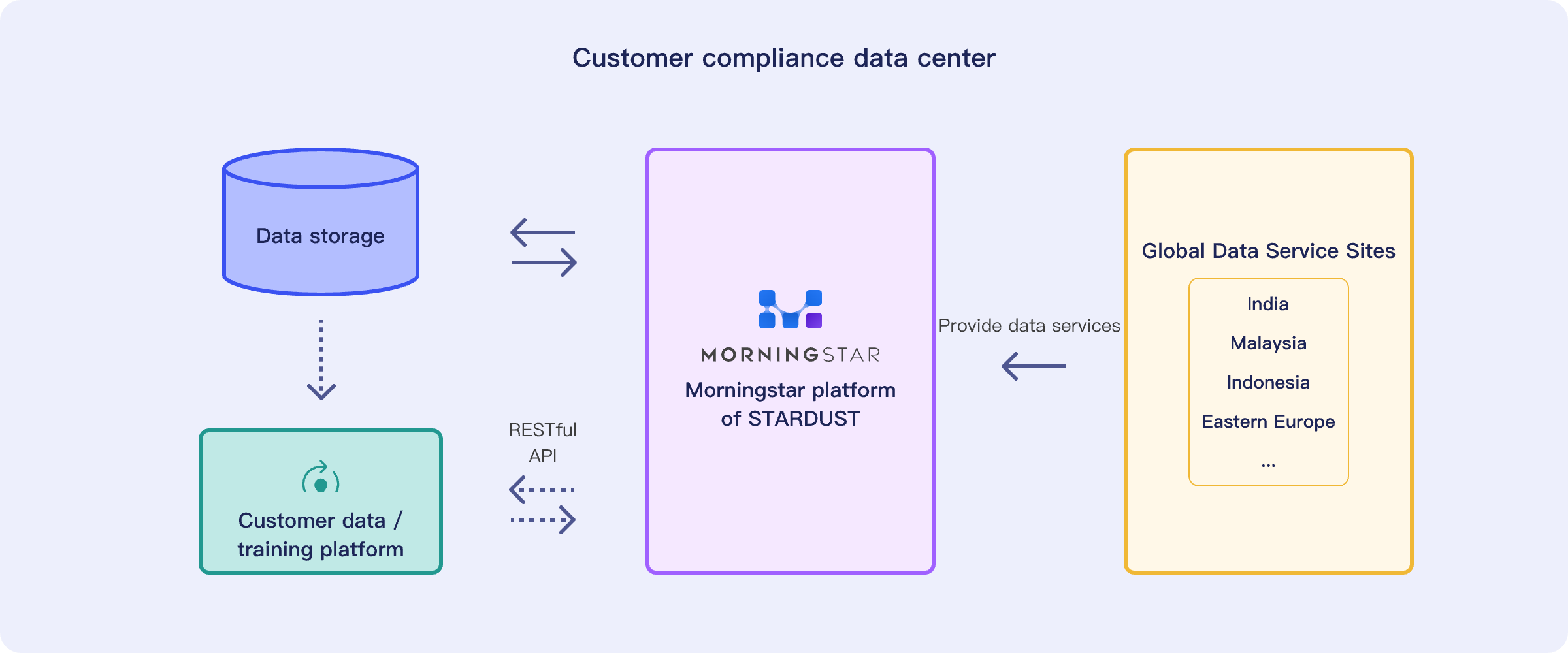
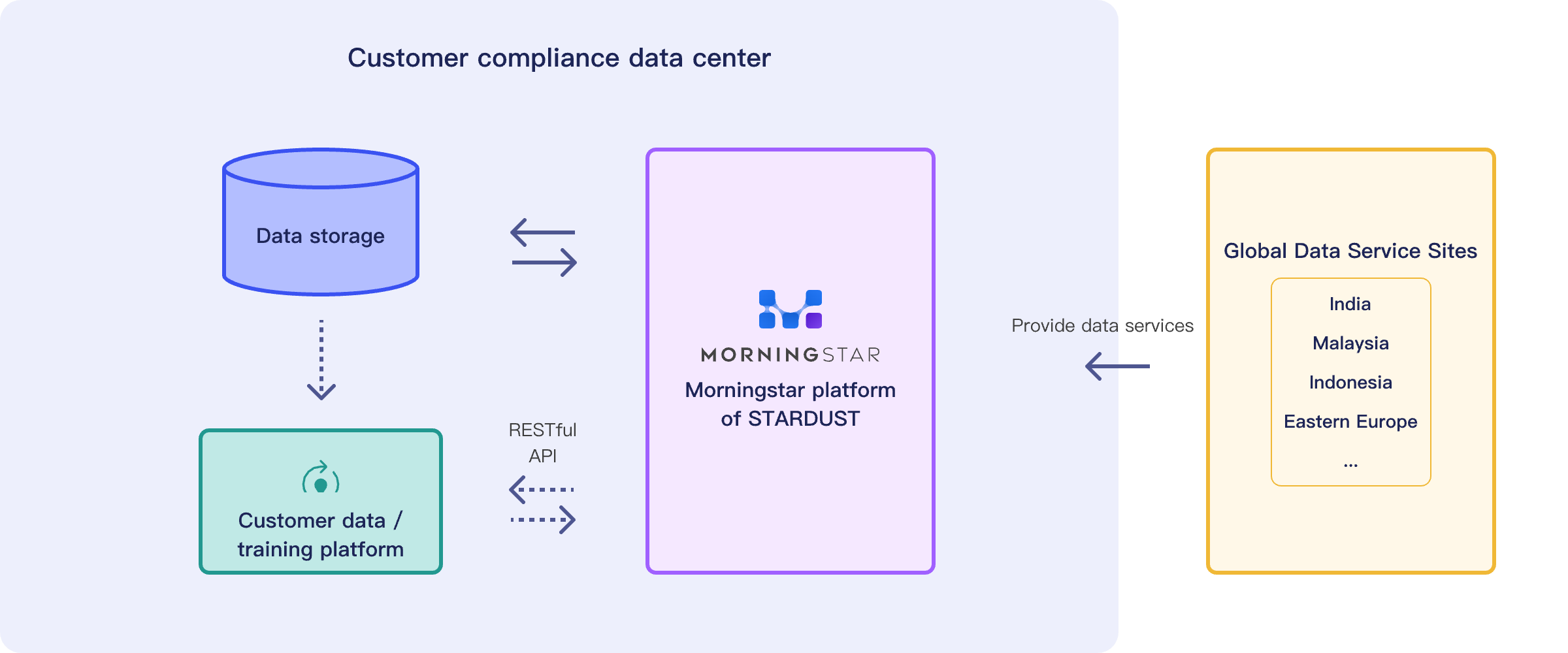
Access Security
Utilize HTTPS, AKSK, temporary tokens, and other security technologies.
Data Storage
Utilize highly secure cloud storage where access for upload, download, and modification requires key authentication.
Content Encryption
Support data encryption to prevent downloads from web pages.
Prevention of Propagation
Implement dynamic watermarking in the system for traceability and to prevent information dissemination.
Hardware Security
Enforce designated device operations, disable USB ports on hardware to prevent unauthorized data copying.
Secure Deployment
Deploy privately on customer premises or in compliant cloud environments to ensure data remains within the domain.
Access Control
Access management systems require fingerprint authentication for personnel entry and exit.
Workplace Monitoring
Monitor devices and view the work environment through real-time cameras.
User Authentication
Facial recognition with ID verification.
Proposal 1
Proposal 2
Proposal 3


Explore More
Fill out the form to schedule a personalized demo with our team. Experience firsthand how our innovative solutions can meet your needs and drive success.
Copyright © 2025 StardustAI Inc. All rights reserved.